Cyber Security Awareness
Cybersecurity has become one of the biggest hot topics both inside and outside of technology circles over the last two years. From securing learning devices due to a rise in digital learning during the COVID-19 pandemic, to coping with the fallout of high-profile breaches of several California Community Colleges and K-12 Districts, there is a seemingly endless press dedicated to cybersecurity mishaps and concerns. And with this onslaught of negative news, it can be easy for everyday individuals to become overwhelmed and to feel powerless in the face of the “insurmountable” threats posed by cybersecurity. But in actuality nothing could be further from the truth.
With all of the jargon that is typically thrown around in relation to cybersecurity there is a longstanding misperception that cybersecurity is beyond everyday people and that it should be left to the professionals. Moreover, there is a prevailing sense among the public that breaches are simply a fact of life and that we should just learn to deal with them. But this just isn’t true. In fact, everyday people have a huge role to play in cybersecurity threat prevention, detection, and remediation. For example, according to IBM, 95% of breaches have human error as a main cause. Therefore, everyday day technology users are very much the first line of defense when it comes to thwarting cybercrime.
Phishing
Chaffey college staff and faculty receive phishing attempts on a daily basis. These attacks can take many forms, but they all share a common goal – getting you to share sensitive information such as login credentials, credit card information, or bank account details. Although we maintain controls to help protect our networks and computers from cyber threats, we rely on you to be our first line of defense. Below, are a few different types of phishing attacks to watch out for:
In this type of attack, hackers impersonate a real company to obtain your login credentials. You may receive an e-mail asking you to verify your account details with a link that takes you to an imposter login screen that delivers your information directly to the attackers.
Spear phishing is a subset of phishing that is more personalized. The communication is customized and directed at the recipient making the attacker seem like a legitimate source. They may have more details about you, use your name or phone number, and refer to your position here at Chaffey to trick you into thinking they have a connection to you.
Whaling is a popular ploy aimed at getting you to transfer money or send sensitive information to an attacker via email by impersonating Chaffey management. Using a fake domain that appears similar to ours or an email with the manager's name embedded, they otherwise look like normal emails, often from the President, Executive Team members, or Deans/Directors, asking you for your cell number to try to start a one-on-one conversation. Once they begin communicating with you they will ask you to purchase e-gift cards for them or send sensitive information (including usernames and passwords).
You may receive an e-mail that appears to come from file-sharing sites like Dropbox, DocuSign, OneDrive, AdobeSign, or Google Drive alerting you that a document has been shared with you or needs your review/signature. The link provided in these e-mails will take you to a fake login page that mimics the real login page and will steal your account credentials.
What You Can Do
To avoid these phishing schemes, please observe the following email best practices:
- Above all else: Do not click on links or attachments from senders that you do not recognize. Be especially wary of .zip or other compressed or executable file types.
- If something looks Phishy, it probably is.
- Do not provide sensitive personal information (like usernames and passwords) over email.
- Watch for email senders that use suspicious or misleading domain names.
- Inspect URLs carefully to make sure they’re legitimate and not imposter sites.
- Do not try to open any shared document that you’re not expecting to receive.
- When in doubt, contact the ITS Help Desk.
- Be especially cautious when opening attachments or clicking links if you receive an email containing [EXT] in the subject or containing the warning banner indicating that it originated from an external source.
Ransomware
Ransomware is increasingly being used by hackers to extort money from educational institutions (You may have seen the LAUSD articles in the news last week). Ransomware is a type of malicious software that takes over your computer, encrypting your files until you pay a ransom.
Although we maintain controls to help protect our networks and computers from this type of attack, with the quickly changing attack scenarios we rely on you to be our first line of defense.
Here are some simple things you can do to help Chaffey avoid a ransomware/malware attack:
Think Before You Click
The most common way ransomware enters corporate networks is through email. Often, scammers will include malicious links or attachments in emails that look harmless. To avoid this trap, please observe the following email best practices:
- Do not click on links or attachments from senders that you do not recognize. Be especially wary of .zip or other compressed or executable file types.
- Do not provide sensitive personal information (like usernames and passwords) over email.
- Watch for email senders that use suspicious or misleading domain names.
- If you can’t tell if an email is legitimate or not, please contact the ITS Help Desk.
- Be especially cautious when opening attachments or clicking links if you receive an email containing the [EXT] tag in the subject line and/or the warning banner in the body of the email, indicating that it originated from an external source.
Backup your files
Backing up your files to OneDrive, an external hard drive, and/or a USB thumb drive is one of the easiest ways to mitigate the risk of ransomware. In the case of a ransomware attack, ITS can wipe/re-image your computer and you can restore your files from your backup. A popular approach is to follow the 3-2-1 rule. Keep 3 separate copies of your files on 2 different storage types with 1 copy offline.
If Something Seems Wrong, Notify ITS
If your computer is infected with ransomware, you will typically be locked out of all programs and a “ransom screen” will appear. In the unfortunate event that you click a link or attachment that you suspect is malware or ransomware, please notify IT immediately.
Strong Passwords and Password Managers
The easiest way to protect yourself, and Chaffey, from cyber threats is by having a strong password. It’s simple – the longer and more complex your password, the more difficult it is to crack.
Hackers have created databases of the most common words, phrases, and number combinations that they can run your password through to find a match. The following are some common password themes that you should avoid:
- Birthdays;
- Names;
- Phone numbers;
- Sports teams;
- Chaffey information; and
- Simple obfuscation of a common word (“P@$$w0rd”).
To start, your password should be at least 15 characters long, with at least one capital letter, one number, and one special character (“@”, or “%”, etc.). As an added layer of security, change your passwords on a regular basis to ensure that you stay ahead of the hackers. And, whenever possible, you should use MFA (multi-factor authentication) or 2FA (two factor authentication) to add an extra layer of security to your accounts and applications.
Remember, the best passwords contain as much randomness as possible – using unlikely combinations and random characters is a great strategy. Be creative!
Bad: Fuzzydog82
Better: %FuZZyD0G#8254!
Best: myFuzzyDog-eats4bones!Aday-BIG$
Passwords should not be shared with anyone, including your supervisors. In situations where someone requires access to another individual’s protected resources, delegation of permission options should be explored or contact ITS for assistance. For example, Microsoft Exchange calendar will allow a user to delegate control of his or her calendar to another user without sharing any passwords. ITS staff will never ask for your password, not even for the purpose of computer repair or software install.
It’s important to remember that you should not use the same password for multiple accounts – no matter how strong it is – because that’s not safe. If your one password gets compromised it can be used to gain access to all your accounts and your sensitive information. But, password managers are easy to use and make a big difference.
Password managers allow you to use unique passwords for the ever-increasing number
of online accounts we use at Chaffey and at home. A password manager is software created
to manage all your online credentials like usernames and passwords. It stores them
in a safe, encrypted database and generates new passwords when needed.
Because the password manager stores all your passwords, you don’t need to memorize hundreds of passwords or keep that secret password paper in your drawer. You would only need to remember one to unlock your password vault in the manager app, so it makes things so much easier.
Password manager options.
There are many different free or paid password managers available for personal use, and several options for use on systems here at Chaffey. Some examples Include:
- Keeper (for home use; available as Self Service install on Chaffey IOS, Mac OSX, and PC devices)
- 1Password (for home use; available as Self Service install on Chaffey IOS, and Mac OSX devices)
- KeePass (for home use; available as Self Service install on Chaffey IOS, and PC devices)
- LastPass (for home use; available as Self Service install on Chaffey IOS devices)
- Bitwarden (for home use)
Software Updates
One way to keep your information secure is to keep your software and apps up to date. While Chaffey ITS manages your district owned devices for you, it is important for you to keep your home computers and mobile devices up to date.
Always keep your software updated when updates become available and don’t delay. These updates fix general software problems and provide new security patches where criminals might get in. You can be sure the bad guys are always looking for new ways to get to your data through software, so updating your software is an easy way to stay a step ahead.
When downloading a software update, only get it from the company that created it. Never use a hacked, pirated, or unlicensed version of software (even if your friend gave it to you). These often contain malware and cause more problems than they solve.
Software from legitimate companies usually provides an option to update your software automatically. When there’s an update available, it gives a reminder so you can easily start the process. If you can’t automatically update it, remind yourself to check quarterly if an update is available.
ITS automatically provides critical updates and service packs to district owned devices for a wide range of software products (Microsoft. Adobe, Google Chrome, Zoom, etc). Many of these updates require the device be connected to our Ethernet network. We recommend that you bring in your district owned devices and connect them to the Chaffey network regularly. If you need assistance or have question about the currency of a software product/application, please contact the ITS Help Desk.
Maybe you’ve seen these pop-up windows when visiting a website or opening software that urgently asks you to download something or fill out a form? These are always fake and should not be followed. A browser will only warn you not to move forward or stay on a specific web address because it might not be secured or it could contain malware.
Additional Resources
Cybersecurity 101 Tip Sheet (CISA)
Why is Cybersecurity Important? (CISA)
Software Updates Infographic (NCSA)
Software Updates (NCSA)
Understanding Patches and Software Updates (CISA)
Information Security Awareness Training
As you are aware, Chaffey College is more reliant than ever on technology and the network. The security of those resources has become an increasingly high priority. To help protect our confidential assets, and to comply with State and Federal requirements, it is necessary for all district employees to complete an Information Security Awareness. While our objective is to meet all compliance and legal requirements, our overarching goal is to educate and protect our staff and administration by changing their online behaviors and encouraging safe practice.
The Technology Committee has selected a self-paced training program that is available via the “My Learning Hub” link on the Chaffey Portal dashboard page (see directions below). This training will not only comply with regulations but will also help protect our confidential information and assets. Most importantly, it will promote safe practices for our community regarding potential risks and rapidly evolving threats that target online behavior.
The District expects that training will be required annually for all staff and faculty, full and part-time. Full-time faculty will complete this training as part of their professional responsibilities, as outlined under 18.2.3 in the Collective Bargaining Agreement, and all part-time faculty who complete it will be compensated one-hour at the training rate.
Staff and Faculty can access the self-paced training in My Learning Hub (directions below) through the College Portal. The training module should take approximately 30 minutes. This training is due at the beginning of each calendar year and must be completed no later than January 31st.
Directions for Accessing Training Module:
If the link doesn’t work, please follow these instructions:
Log into the Chaffey Portal and locate My Learning Hub
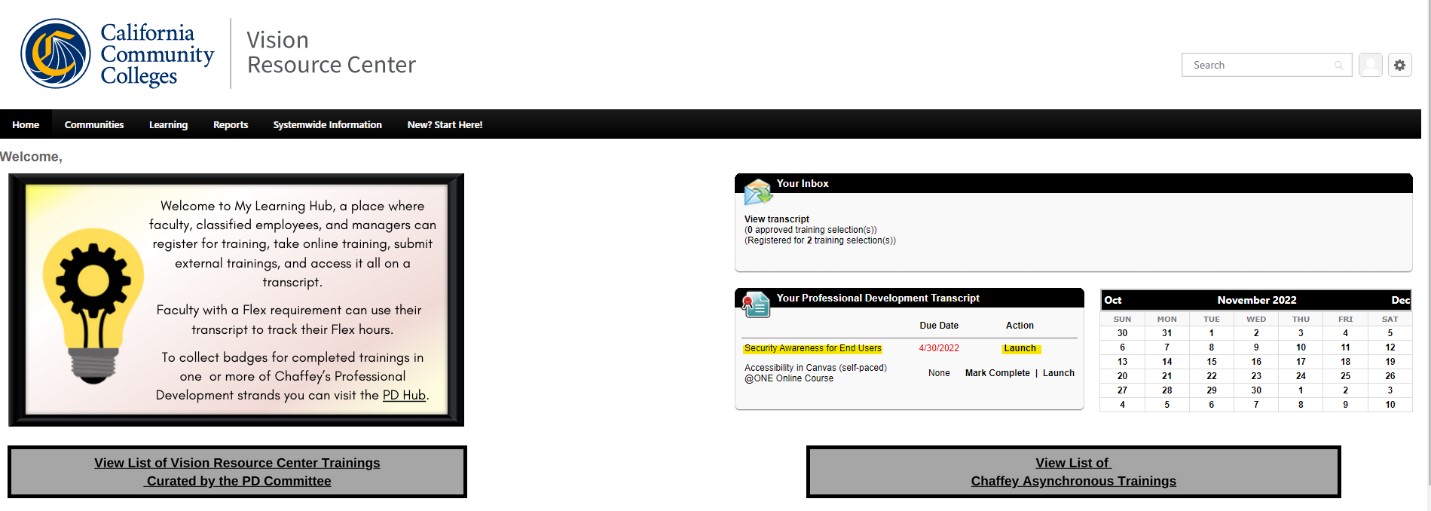
Once you're logged into My Learning Hub, the right-hand corner will show the Security Awareness training that is ready for you for begin.
About Cybersecurity Awareness Month
National Cybersecurity Awareness Month is co-led by the National Cyber Security Alliance (NCSA) and the Cybersecurity and Infrastructure Security Agency (CISA) of the U.S. Department of Homeland Security.
For more information about ways to keep you and your family safe online visit https://staysafeonline.org/cybersecurity-awareness-month/ and/or cisa.gov/ncsam.
H6: Other Resources
Please contact the Help Desk at ext. 6789 or ISRepairs@Chaffey.edu if you have any questions or would like additional information.


